Once on a single Cisco 6509e switch configured as L3 and with a standard CPU load of 10%, the load suddenly increased to 40%.
Continue reading “Cisco 6509e Net Input CPU Load”Tag Archives: virus
Some information about the virus encryptor Trojan.Encoder.12544 attacked 06/27/2017
06/27/2017 After lunch, I received a call from one organization and reported that many computers stopped working, but some worked, I understood that Windows auto-update was enabled and all updates were installed, including the critical vulnerability fix that the virus uses – Microsoft Security Bulletin MS17-010 – Critical
On some infected computers, there was the following window (infected MBR area):
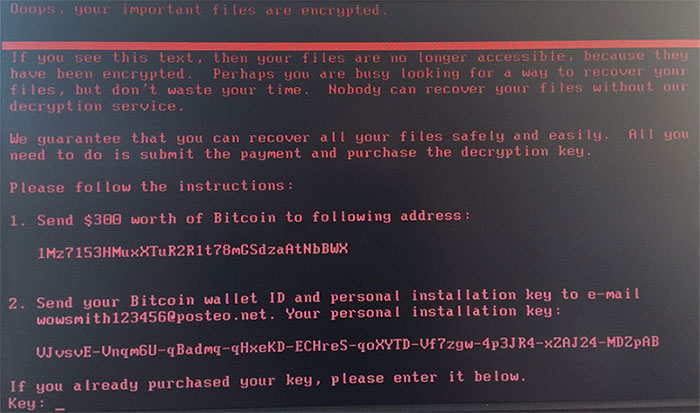
On the other side, the disk was checked for errors via CHDISK, as it turned out to be the second stage of the virus – disk encryption using AES-128-CBC algorithms and in this case, an immediate shutdown is necessary to recover the remaining unencrypted data.
Through special utilities, you could see only a few unencrypted data that can be recovered, and the rest can only be returned from backup copies made by system administrators since the decryptor is not available at the moment.
Under the old version of the virus last year, the decryptor was written https://github.com/leo-stone/hack-petya
The mail that was specified for requesting the decryption key was blocked after some time after the virus appeared, even about 45 transactions were received on the wallet.